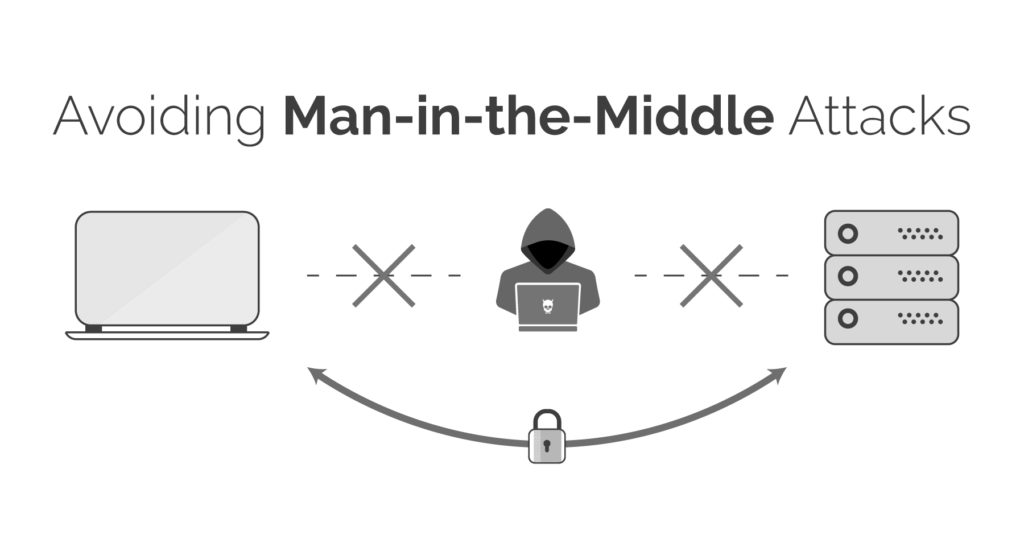
Man in the middle attacks
A man-in-the-middle (MitM) attack is when an attacker intercepts communications between two parties either to secretly eavesdrop or modify traffic traveling between the two. Attackers might use MitM attacks to steal login credentials or personal information, spy on the victim, or sabotage communications or corrupt data. A man-in-the-middle attack requires three players. There’s the victim, the entity with which the victim is trying to communicate, and the “man in the middle,” who’s intercepting the victim’s communications. Critical to the scenario is that the victim isn’t aware of the man in the middle. The attack is a type of eavesdropping in which the entire conversation is controlled by the attacker. Sometimes referred to as a session hijacking attack, MiTM has a strong chance of success when the attacker can impersonate each party to the satisfaction of the other. MiTM attacks pose a serious threat to online security because they give the attacker the ability to capture and manipulate sensitive information in real-time.
A common method of executing a MiTM attack involves distributing malware that provides the attacker with access to a user’s Web browser and the data it sends and receives during transactions and conversations. Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example, the Transport Layer Security (TLS) protocol can be required to authenticate one or both parties using a mutually trusted certification authority.
Types of MitM attacks.
Cybercriminals can use MitM attacks to gain control of devices in a variety of ways. There are 7 types of this attack.
1. IP spoofing: Every device capable of connecting to the internet has an internet protocol (IP) address, which is similar to the street address of home. By spoofing an IP address, an attacker can trick user into thinking they’re interacting with a website or someone its not, perhaps giving the attacker access to information user otherwise would not share.
2. DNS spoofing: Domain Name Server, or DNS, spoofing is a technique that forces a user to a fake website rather than the real one the user intends to visit. When a use becomes a victim of DNS spoofing, user may think he is visiting a safe, trusted website when in reality he is actually interacting with a fraudster. The attacker’s goal is to divert traffic from the real site or capture user login credentials.
3. HTTPS spoofing: When doing business on the internet, seeing “HTTPS” in the URL, rather than “HTTP” is a sign that the website is secure and can be trusted. In fact, the “S” stands for “secure.” An attacker can fool a web browser into believing it’s visiting a trusted website when it’s not. By redirecting the browser to an unsecure website, the attacker can monitor users’ interactions with that website and possibly steal personal information user is sharing with the website.
4. SSL hijacking: When a device connects to an unsecure server — indicated by “HTTP” — the server can often automatically redirect user to the secure version of the server, indicated by “HTTPS.” A connection to a secure server means standard security protocols are in place, protecting the data user share with that server. SSL stands for Secure Sockets Layer, a protocol that establishes encrypted links between web browser and the web server. In an SSL hijacking, the attacker uses another computer and secure server and intercepts the entire information passing between the server and the user’s computer.
5. Email hijacking: Cyber criminals sometimes target email accounts of banks and other financial institutions. Once they gain access, they can monitor transactions between the institution and its customers. The attackers can then spoof the bank’s email address and send their own instructions to customers. This convinces the customer to follow the attackers’ instructions rather than the banks. As a result, an unwitting customer may end up putting money in the attackers’ hands.
6. Wi-Fi eavesdropping: Cyber criminals can set up Wi-Fi connections with very legitimate sounding names, similar to a nearby business. Once a user connects to the attackers Wi-Fi network, the attacker will be able to monitor the victims’ online activity and be able to intercept login credentials, payment card information, and more. This is just one of several risks associated with using public or unprotected Wi-Fi networks.
7. Stealing browser cookies: A browser cookie is a small piece of information a website stores on user’s computer. For example, an online retailer might store the personal information user enters and shopping cart items user have selected on a cookie so user don’t have to re-enter that information when he return to the website. A Cyber-criminal can hijack these browser cookies. Since cookies store information from user’s browsing session, attackers can gain access to user’s passwords, address, and other sensitive information.
You May also like these articles.
You can buy the book which covers all the topics.