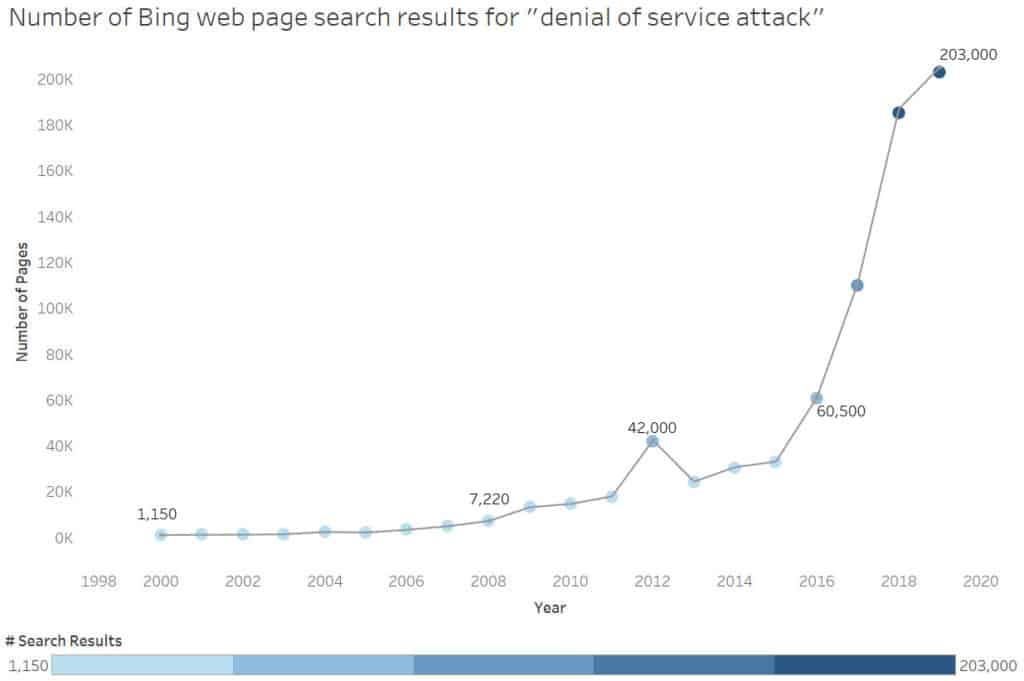
What is DoS Attack ?
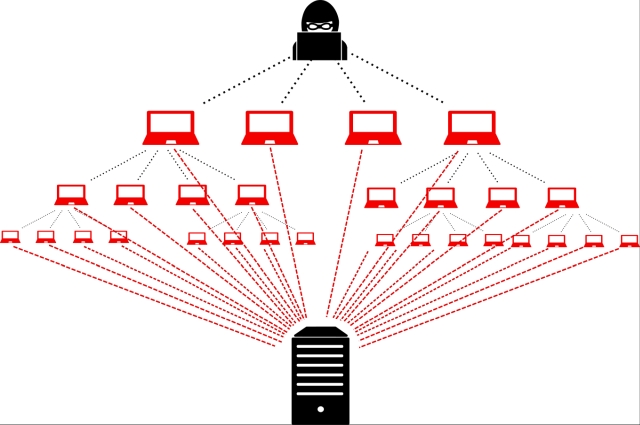
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. Distributed denials of service (DDoS) attacks are a subclass of denial of service (DoS) attacks. Unlike other kinds of Cyber-attacks, DDoS assaults don’t attempt to breach users security perimeter. Rather, a DDoS attack aims to make victims website and servers unavailable to legitimate users. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination.
DDoS can also be used as a smokescreen for other malicious activities and to take down security appliances, breaching the target’s security perimeter. DDoS attacks can come in short bursts or repeat assaults, but either way the impact on a website or business can last for days, weeks and even months, as the organization tries to recover. The differences between regular and distributed denial of service assaults are substantive.
In a DoS attack, a perpetrator uses a single Internet connection to either exploit software vulnerability or flood a target with fake requests—usually in an attempt to exhaust resources such a RAM, CPU, Bandwidth etc. On the other hand, distributed denials of service (DDoS) attacks are launched from multiple connected devices that are distributed across the Internet. These multi-person, multi-device barrages are generally harder to deflect, mostly due to the sheer volume of devices involved. Unlike single-source DoS assaults, DDoS attacks tend to target the network infrastructure in an attempt to saturate it with huge volumes of traffic. The underlying effectiveness of most DDoS attacks comes from the disparity between the amount of resources it takes to launch an attack relative to the amount of resources it takes to absorb or mitigate one.