Non-Repudiation and Trust in Digital Systems
In the digital world, trust is not built on handshakes or verbal promises. Instead, it relies on systems that can […]

In the digital world, trust is not built on handshakes or verbal promises. Instead, it relies on systems that can […]

In cybersecurity, preventing unauthorized access is only part of the challenge. Equally important is knowing what happens inside systems once […]

In cybersecurity, access control is not a single action but a sequence of related steps that work together to protect […]

When people think about cybersecurity, they often focus on keeping information secret or preventing unauthorized changes. However, an equally important […]
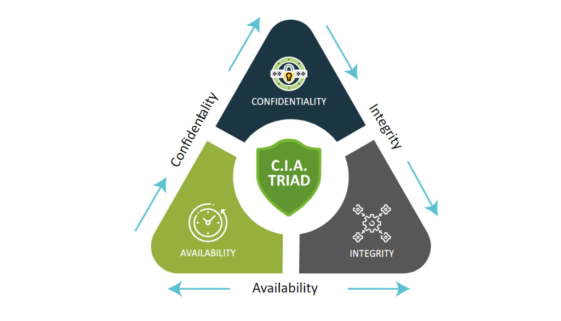
When people begin learning about cybersecurity, one concept appears repeatedly and forms the foundation of almost everything that follows: the […]