What is C I A Triad ?
In order to define the Cyber Security one needs to have Understanding of the significance of the three foundational information security principles: Confidentiality, Integrity, and Availability, otherwise known as the CIA Triad. The concept of the CIA triad formed over time and doesn’t have a single creator. Confidentiality it may have been first proposed as early as 1976 in a study by the U.S. Air Force. Likewise, the concept of integrity was explored in a 1987 paper titled “A Comparison of Commercial and Military Computer Security Policies.” The paper recognized that commercial computing had a need for accounting records and data correctness. Even though it’s not as easy to find an initial source, the concept of availability became more widespread one year later in 1988. By 1998 people saw the three concepts together as the CIA triad.
- Confidentiality – information is not disclosed to unauthorized individuals.
- Integrity – ensuring accuracy and completeness of data.
- Availability – users must have information when they need it.
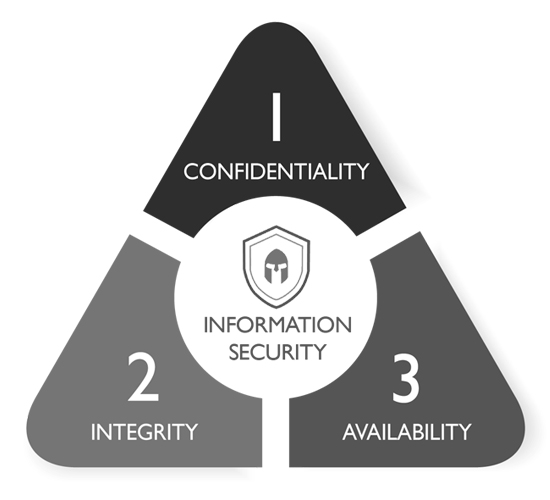
The CIA Triad is a central tenant of ISO/IEC 27001:2013 (ISO 27001), the international standard that describes best practice for an ISMS (information security management system). ISO 27001 neatly summarizes Information security as the maintenance of confidentially, availability and integrity of the confidential assets of an organization
CIA Triad is a model designed to guide policies for information security. It provides us with a reference to evaluate and implement secure information systems, independently of the underlying technologies. Each one has specific requirements and processes. CIA Triad is aimed at protecting the organization’s digital assets against the ever-growing Cyber-attacks. This can be ensured by deploying appropriate security controls to provide several security features such as deterrent, prevention, and detection of Cyber-crimes. In this context, confidentiality is a set of rules that limits access to information, integrity is the assurance that the information is trustworthy and accurate, and availability is a guarantee of reliable access to the information by authorized people. Lets look at components of CIA Triad individually.
Confidentiality:
Confidentiality is roughly equivalent to privacy. Confidentiality ensures privacy to the sensitive information while it is in transit over a network. Proactive measures undertaken to ensure confidentiality are designed to prevent sensitive information from unauthorized people / processes, while making sure that only authorized people and only to the intended parties have access to it. The malicious actors must not intercept the data to use it for nefarious purposes. It is common for data to be categorized according to the amount and type of damage that could be done should it becomes accessible to authorized people / processes. There are various implementations which can be incorporated to ensure the confidentiality of data. Safeguarding data confidentiality involves special trainings for those needs to access and work on sensitive data. These training would typically include understanding of security risks that could compromise the Confidentiality. Training can help users to get familiarize with risk factors and how to safeguard against common attacks. Further aspects of training should include password-related best practices and information about social engineering methods, to prevent users from bending data-handling rules with good intentions and potentially disastrous results.
An example of methods used to ensure confidentiality is an account number or token number when banking online. Cryptography is the best solution in this regard. Data encryption is one of the most common and robust method of ensuring confidentiality. The encryption mainly ensures the confidentiality of sensitive data. It converts the plaintext of data into the Cipher-text, which is an unreadable form for humans. Cipher text can only be understood by the authorized entities. Encryption might involve one of the two vital security controls either Symmetric Encryption or Asymmetric Encryption. User IDs and passwords constitute a standard procedure; two-factor authentication is also being implemented in most online banking transactions. Other options include biometric verification and security tokens, soft or hardware tokens. Users can also take precautions to minimize the number of places where the information appears and the number of times it is actually transmitted to complete a transaction. Extra measures might be taken in the case of extremely sensitive data, such as storing only on air gapped computers and networks, disconnected storage devices for highly sensitive information, in hard copy form only. In addition, user can also use Steganography to hide data into another type of data such as images, audio, or video files. Hidden sensitive data in large media files is much difficult to compromise.
Confidentiality should ensure that
- Data should be handled based on their required privacy.
- Data should be encrypted, with a form of two-factor authentication to reach it.
- Keeping access control lists and other file permissions up to date.
Integrity:

Integrity involves maintaining the consistency, accuracy, and trustworthiness of data over its entire life cycle. Integrity refers to preventing data from being tampered with, modified, or altered in malicious way to achieve malicious goals. That means data which is sent must be received intact and unaltered by an authorized party. Data must not be changed in transit, and steps must be taken to ensure that data cannot be altered by unauthorized people (a breach of confidentiality). Integrity is essential for data whether it is in transit or it is in a storage media. Data integrity is crucial for E-commerce and business websites. These measures include file permissions and user access controls. Version control may be used to prevent erroneous changes or accidental deletion by authorized users from becoming a problem. Various attacks that compromise data integrity include a Man-In-the-Middle (MITM) attack, penetrating into the web server, and introducing malicious code in databases.
In addition, some means must be in place to detect any changes in data that might occur as a result of non-human-caused events such as an electromagnetic pulse (EMP) or server crash. Use of Hashing Algorithms such as MD5 and SHA1 are normally provided by developers in order to check the integrity of data. Other techniques include certificates, digital signatures, and non-repudiation. Some data might include checksums, even cryptographic checksums, for verification of integrity. Backups or redundancies must be available to restore the affected data to its correct state.
Integrity should ensure that
- Employees are knowledgeable about compliance and regulatory requirements.
- Use a backup and recovery software.
- To ensure integrity, make use of version control, access control, data logs and checksums.
Availability:

Availability is also a security service which ensures the constant availability of resources and services to only authorized parties in a timely manner. Availability is best ensured by rigorously maintaining all hardware, performing hardware repairs immediately when needed and maintaining a correctly functioning operating system environment that is free of software conflicts. Reliable hardware must be maintained in order to provide constant services to a large number of customers in any organization. There must be less downtime during upgrades and backup of sensitive data in external drives will be helpful in case of data loss. It’s also important to keep up with all necessary system upgrades. Providing adequate communication bandwidth and preventing the occurrence of bottlenecks are equally important. Quick disaster recovery plans should be followed in worst case scenarios. Other important security controls for availability include data backup, patching, and redundant systems. Redundancy, failover, RAID even high-availability clusters can mitigate serious consequences when hardware issues occur.
Fast and adaptive disaster recovery is essential for the worst-case scenarios; that capacity is reliant on the existence of a comprehensive Disaster Recovery Plan (DRP). Redundancy ensures fault tolerance. It means, when a primary system fails to perform, the secondary system is available to continue the delivery of functions and services. In this case, security analysts redirect all traffic or workload to a backup system. Safeguards against data loss or interruptions in connections must include unpredictable events such as natural disasters and fire. To prevent data loss from such occurrences, a backup copy may be stored in a geographically-isolated location, perhaps even in a fireproof, waterproof safe. Extra security equipment or software such as firewalls and proxy servers can guard against downtime and unreachable data blocked by malicious denial-of-service (DoS) attacks and network intrusions.
Availability
- Use preventative measures such as redundancy, failover and RAID. Ensure systems and applications stay updated.
- Use network or server monitoring systems.
- In case of data loss, ensure a Data Recovery and Business Continuity plan is in place.
You May also like these articles.



